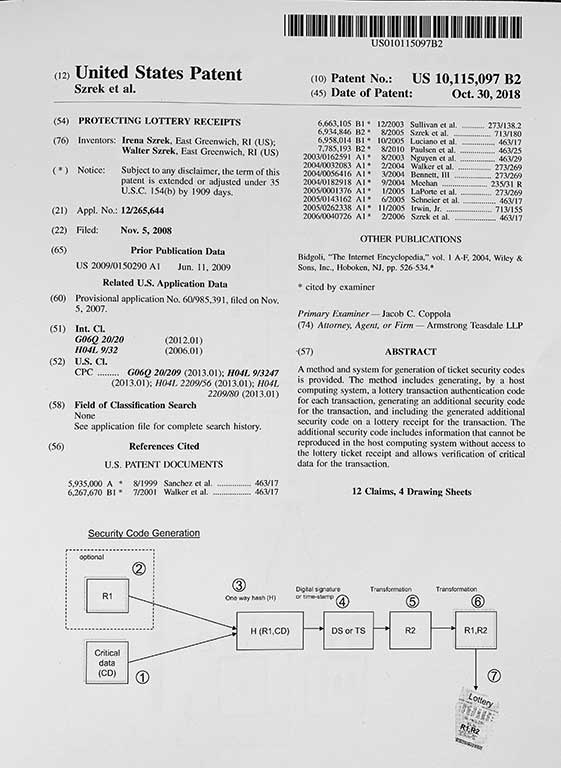
Does certification ensure RNG security?
Certifying an RNG does not usually address security. Certification is important and it is typically done to guarantee randomness, but rarely does it address RNG security. Hence security must be addressed specifically and in a different way.
What kind of security measures are there to protect an RNG?
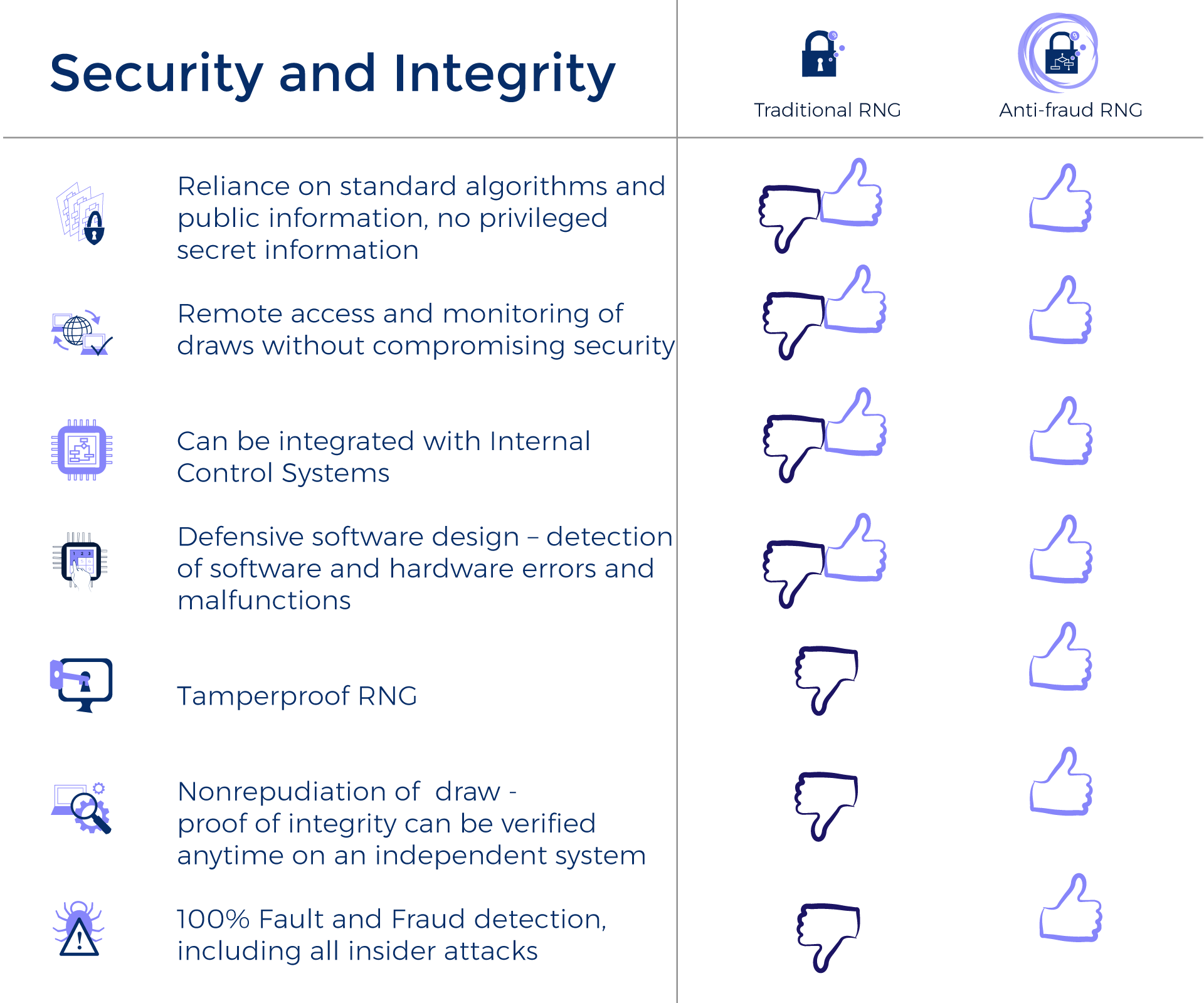
RNG Vendors work with lotteries to establish many important preventive security features that are aimed at limiting access to the RNG (not allowing for an open network, password protection, locks and keys, use of various users to oversee the draw). By limiting access, they protect the RNG from many types of attacks. However, these systems are vulnerable to some types of attacks, particularly attacks from insiders.
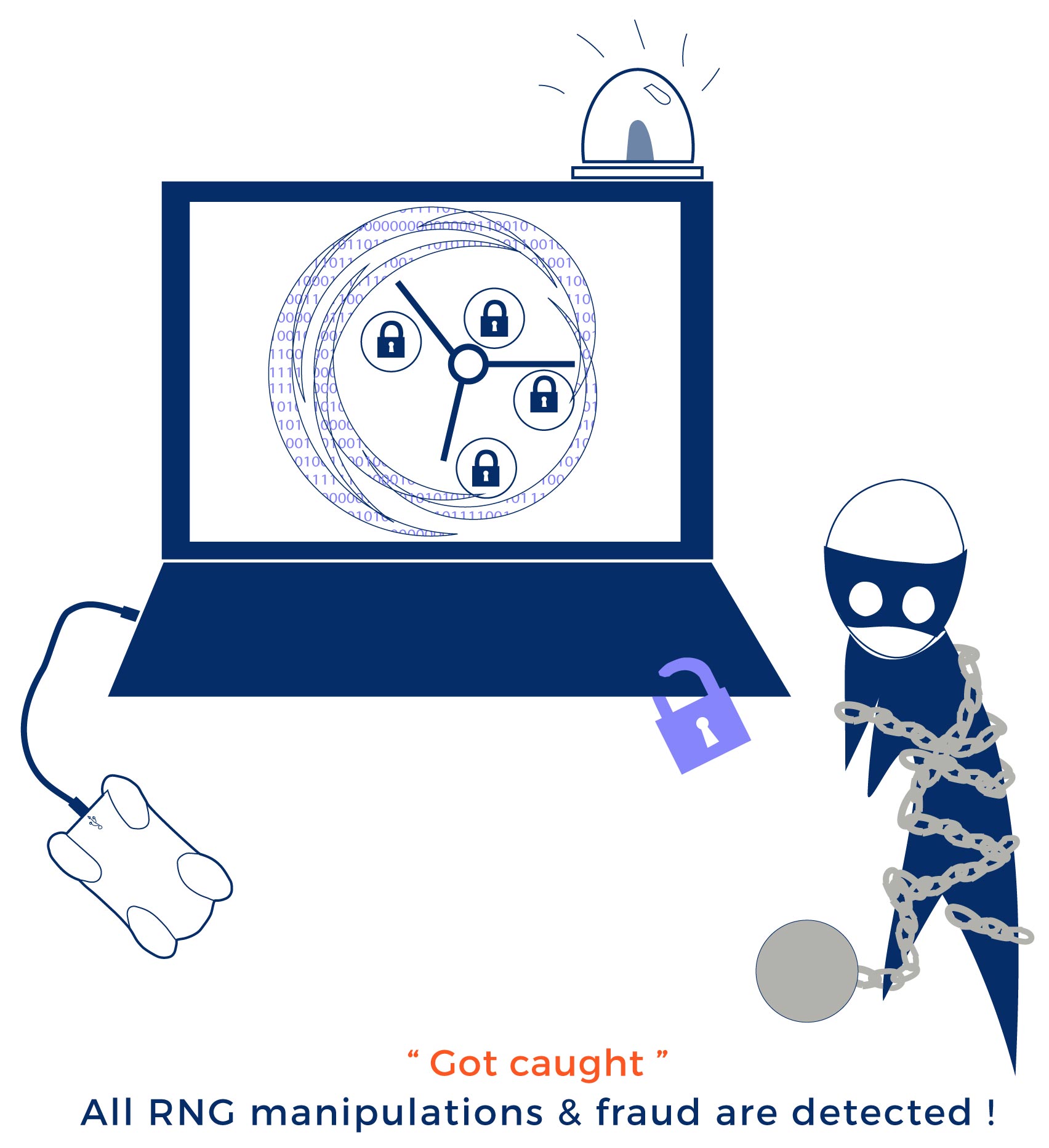
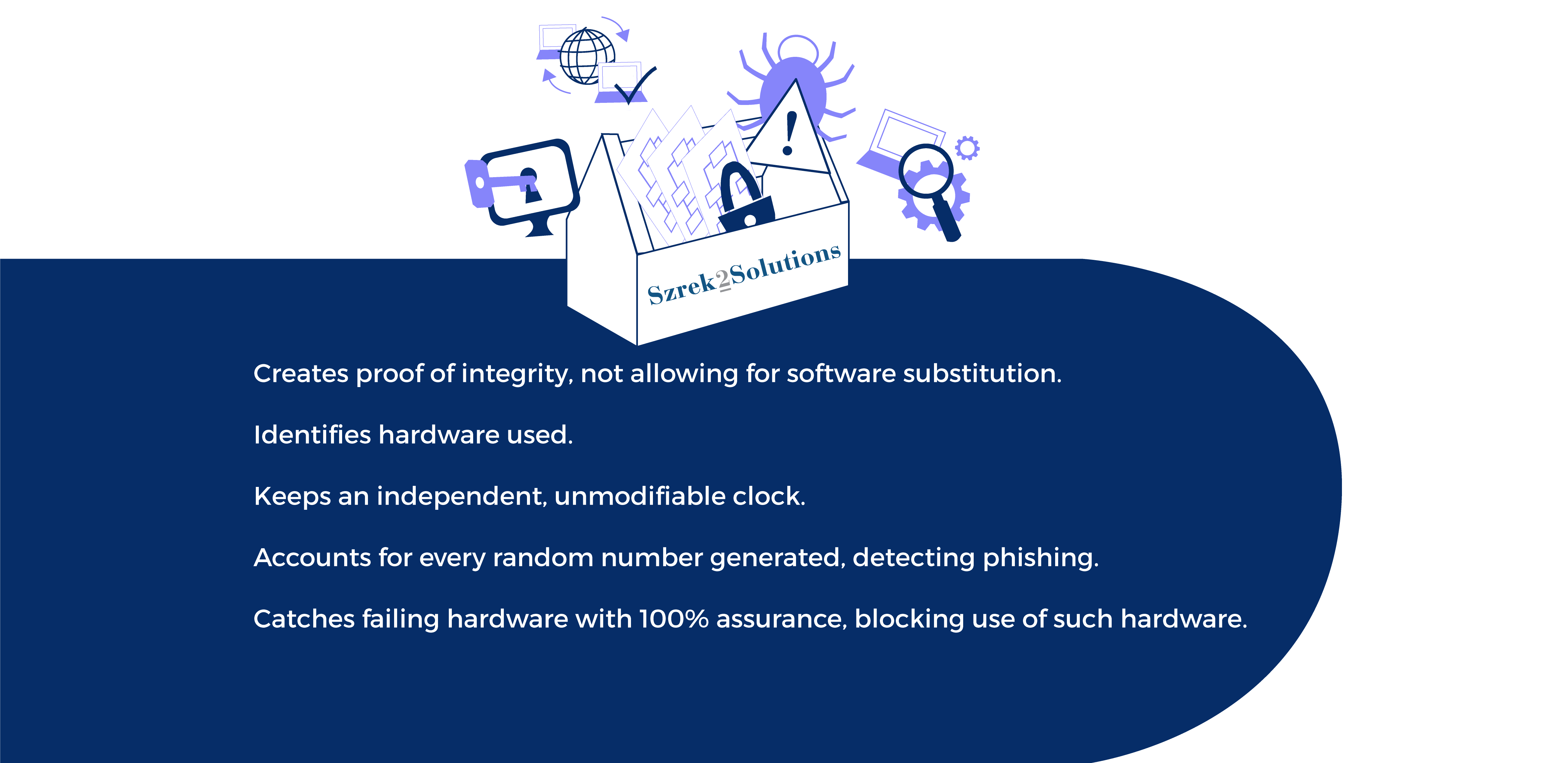
We also introduce protective measures, but our security offers a solution that rests within the system – this is why we say it is a different paradigm. Our technology combines cryptographic hardware and software solutions that enable us to detect traces of any manipulation to the RNG, without relying on anything outside of the system. Manipulations cannot be erased or hidden without leaving a trace, unlike those used by other methods of logs and traces, so trying to break into the RNG will always be useless!
What are the limitations of preventive security?
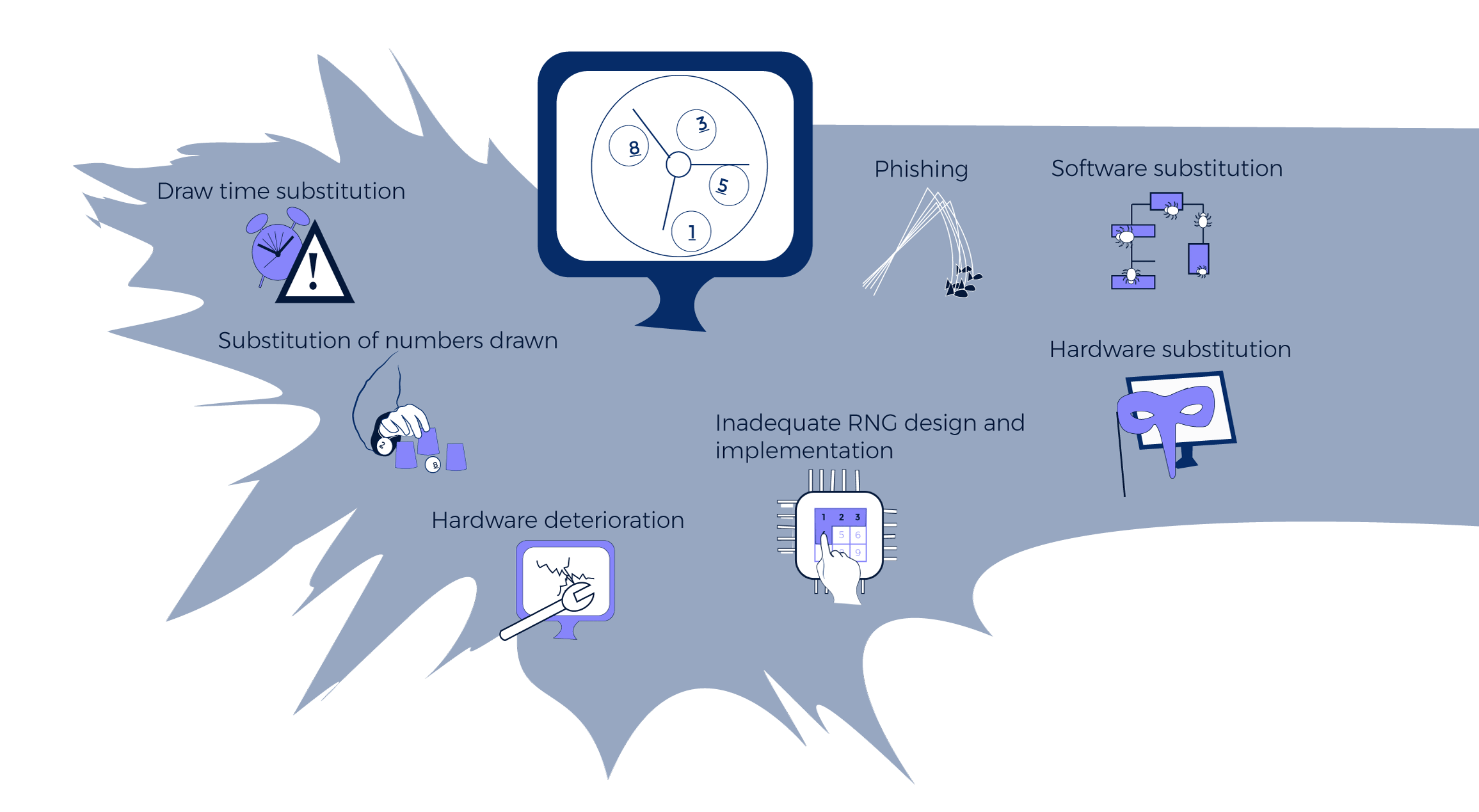
The industry has gained experience from the recent Hot Lotto fraud and other incident about how to respond to known vectors of attack. Although far from perfect, we have some methods for trying to address these attacks. However, with advances in technology there may be new methods of attack forthcoming, and systems are vulnerable to these attacks particularly if they are executed by skilled insiders. This is the limitation of preventive methods – you can only try to prevent against known methods of attack.
This is why you need a methodology that protects against all vectors of attack, known or unknown. Our RNG technology detects every manipulation to the RNG because any manipulation to software, hardware, or otherwise would leave a trace and affect its functioning, causing the RNG and Systemic Independent Audit to have different draw results.
What type of audit is available for RNG systems?
Some people believe that having an auditor present during the draw is sufficient for RNG security, because the auditor by witnessing the draw can verify data consistency and ensure that procedures are followed. However an auditor may not be able to detect what is not visible. For other areas in the lottery, such as gaming systems and lottery tickets, independent system verification is required.
The Szrek2Solutions System offers Systemic Independent Audit that verifies the inner-workings of the RNG, rather the external processes that were used. The Systemic Independent Audit actually uses an independent system to recreate the draw based on the data that the RNG created. This Systemic Independent Audit will recreate the exact same output if the draw was not manipulated. If there was any manipulation, this would affect the data created by the RNG, and then the Systemic Independent Audit would recreate a different draw, providing evidence of tampering with the system.