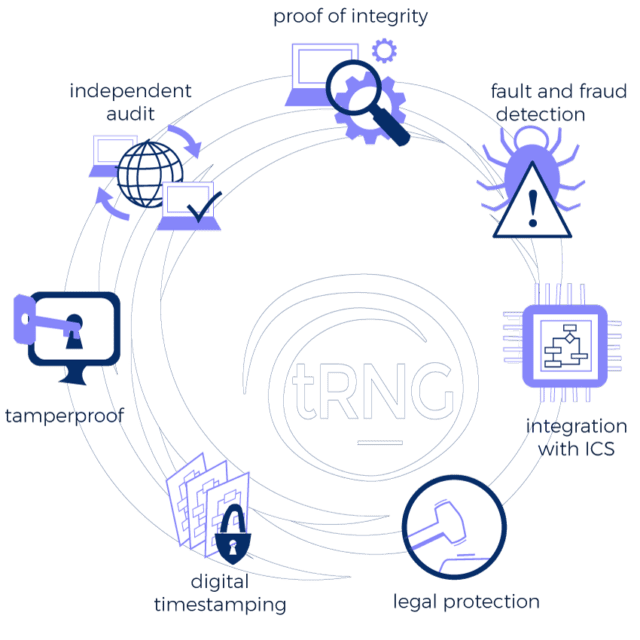
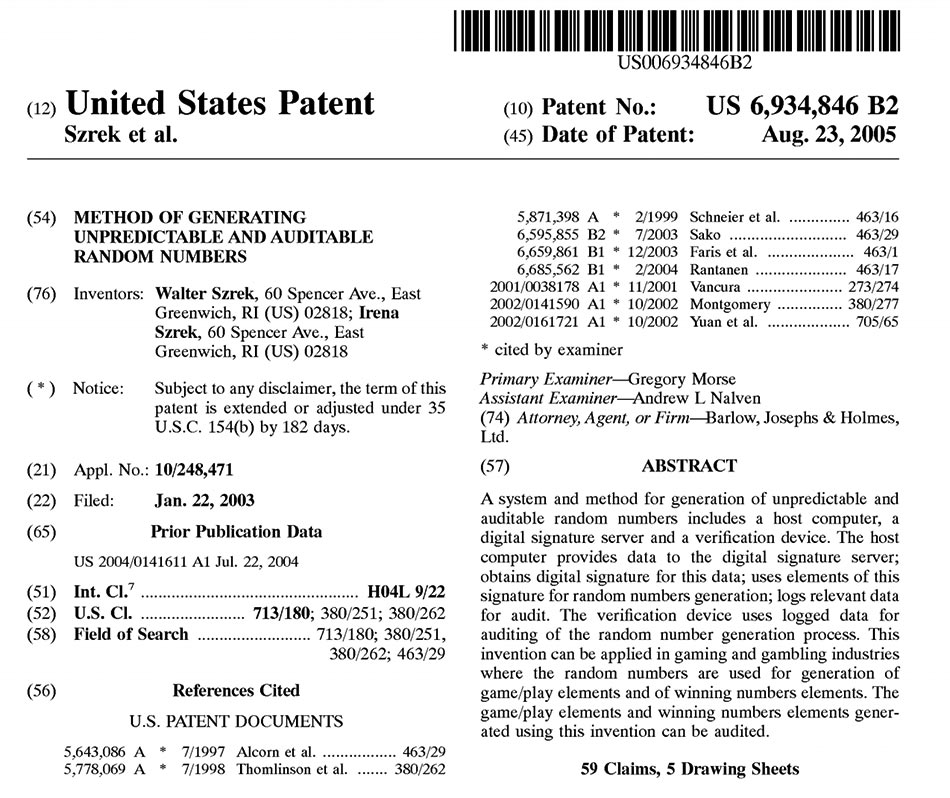
Szrek provides a secure and reliable method for random numbers generation based on its patented method of RNG non-repudiation (patent nr 6,934,846). The method is based on asymmetric properties of digital signatures, where a digital signature generated with a private key is used as a random number seed. Random numbers are derived from the seed, and since the seed is a digital signature of draw data it can be verified using the public key, along with the random numbers and the draw data. For digital
signing, Trusted Draw uses secure and tamper evident NIST certified Hardware Security Modules (HSMs).
The unique benefit of Szrek RNG technology is that generated unpredictable and unbiased random numbers can be mathematically verified to detect any potential fraud. The RNG has been certified by several US and international independent labs and has been used successfully since 2005 by numerous lottery operators and state licensed lotteries around the world.