Schneier on Major Security Vulnerabilities in Microprocessors
Bruce Schneier on Major Security Vulnerabilities in Microprocessors
We would like to share some comments on the latest blog post from Bruce Schneier, who is a well-known IT Security expert and has a very interesting regular blog.
In this recent post, Schneier writes about major security vulnerabilities in microprocessors that have been discovered lately – called Spectre and Meltdown. Schneier explains, “They have to do with manipulating different ways processors optimize performance by rearranging the order of instructions or performing different instructions in parallel. An attacker that controls one process on a system can use the vulnerabilities to steal secrets elsewhere on the computer.” What does this mean? This means that one bad apple (or app or program) on your phone could steal data from all your other good apples (apps or elsewhere on your computer). The significance of this is great, partly because this can affect applications running in the cloud. So one person could have malicious software running in the cloud and this could steal data from everyone else running the same cloud application.
These kinds of vulnerabilities have been used to steal confidential data from people in the cloud.
Schneier argues that those that have been building microprocessors for the last 20 years have been focused on speed – not security.
For electronic draw machines, the story is similar. In the past, developers of random number generators were focused on randomness – not security. Security was addressed, but only as an afterthought. Companies think about how to secure the RNG after having built it. They have developed various measures to protect the RNG. We call this preventive security – protecting access to the room in which the draw machine is located, locks and chains on the machine, password protection, etc. These steps are important but they do not fully address the problem. That is because we can only prevent against the kinds of vulnerabilities that we can predict!
You can’t defend. You can’t prevent. The only thing you can do is detect and respond.
Bruce Schneier
For low frequency draw games, another of the most common prevention methods has been to take the RNG off-line so that it is not connected to any networks, reducing its exposures.
While offline RNGs may seem to increase security, in reality they significantly increase the cost of operating draws without definite security benefits.
Focusing only on prevention is the wrong way to think about RNG security because:
-
- (as mentioned before) we can only prevent against and enforce defenses for the kinds of issues that we can predict
- there is always the risk of undetected RNG hardware problems
- operational mistakes can happen and
- insiders may be able to overcome defenses and attack in an unexpected way.
RNG security and integrity, like any other kind of security, needs to be addressed at the onset – security and integrity must be part of the initial design of the product.
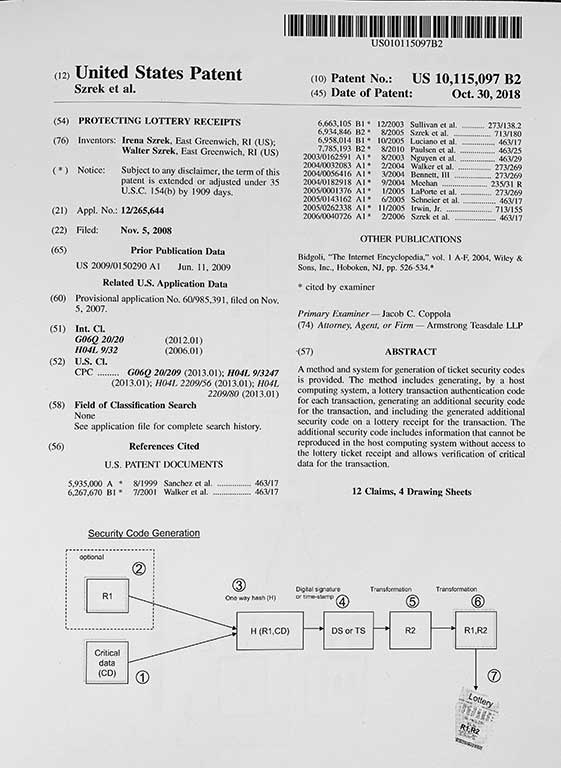
The RNG system must provide nonrepudiation – proof of the origin and integrity of the selected random outcomes, and there must be a way to independently verify that proof. The Szrek RNG provides such non-repudiation.
Security and integrity is our key product differentiator, and our Trusted Suite products are all designed to provide nonrepudiation of the RNG outcomes. As you know, if you’ve been reading about some of our products, if there is any kind of malfunction (e.g. RNG hardware error) or if there is any interference with the system, the system will immediately detect there was a problem! The security paradigm we adhere to is: prevention+ detection + reaction.
Thank you, Bruce, for your great blog and newsletter.