Future-Proof, Tamper-Proof RNG: Discussing the Vulnerabilities of Traditional RNG
future-proof, tamper-proof rng:
discussing the vulnerabilities of traditional rng
We know that complete transparency of the draw process is the key to a trustworthy RNG draw. Our RNG hardware detects any software, hardware, or integrity errors. We have revolutionized the available level of security in the RNG draw, by incorporating 100% fault and fraud detection into the random numbers generation and verification methods.
Traditional RNG security is built around protective security. This type of security has been consistently increasing in most lotteries and RNG vendors have updated their protective security measures. Such measures include background checks of all personnel, the use of only verified vendors, the creation of a secure environment with restricted access, the development of security procedures, role separation for the draw staff, digital signing of draw reports, certification, and code review, etc. In addition, in some locations – including in most US states – RNG machines are designed to be on an isolated system that is not connected to a gaming system. However, even when the RNG is isolated it can be vulnerable to insider attacks, and insider attacks make up the large majority of security breaches across most industries. We refer to traditional RNGs as RNGs that have protective security, as described above, and limited detection capabilities. We note that not all traditional RNGs are alike, and there may be additional security measures used to enhance security. However, unless the RNG system offers all-encompassing fault and fraud detection ensured by nonrepudiation, the RNG system will be vulnerable to obscure faults and insider fraud that can go undetected.
The weakness of traditional draw methods is that they rely highly on processes and people, with limited visibility into the system itself: unexpected problems such as hardware or software errors, or a concealed break-in may not be exposed.
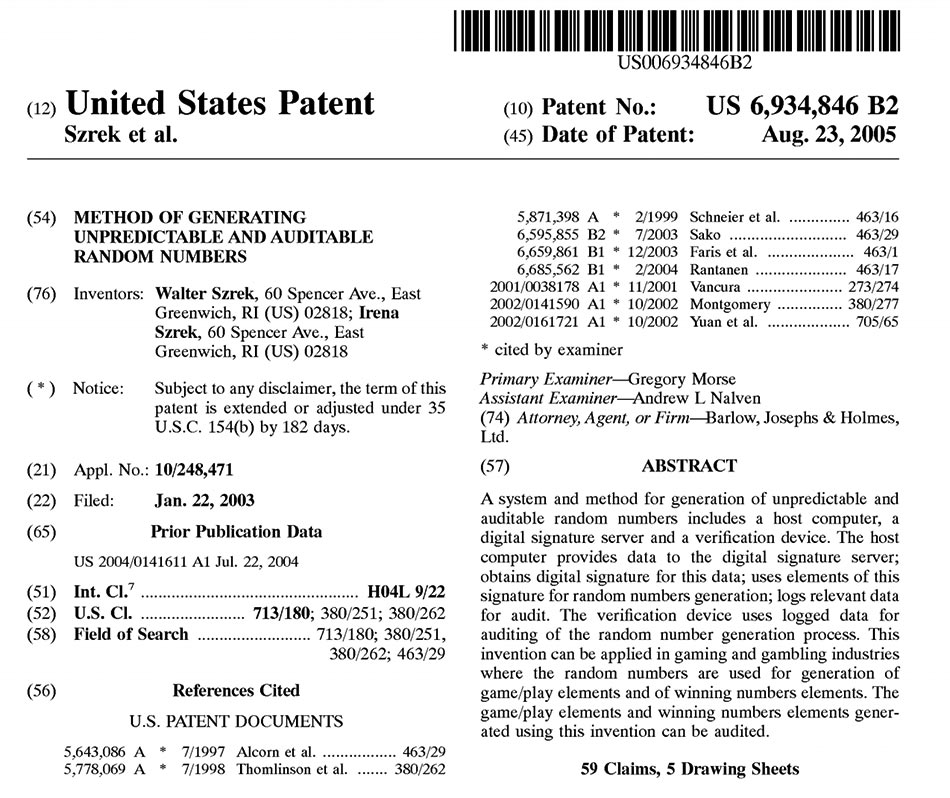
The following are known vulnerabilities of the Traditional RNG system that we have identified:

Software substitution: Fraudulent software is substituted on the certified RNG for a specific draw or draws. We are currently aware of two such methods of attack, (i) a hidden code or a dynamic link library (dll) can be installed on the RNG system at the time when the original code is installed or at a later time, and may be triggered by a specific date or event, (ii) a self-destructive root-kit can be installed on the RNG system at the time of original installation or afterwards, e.g. during system maintenance. In all cases, such software may be very difficult or even impossible to detect because it can be hidden, encrypted, self-destructive, and because it may only run at a specific time. Methods such as certification may not detect such hidden code because it runs only at certain times or is dependent on other conditional factors related to number generation. Pre and post-testing of draws will not detect the hidden code because such tests focus on analyzing statistical distributions. Verification of program checksums may fail because a different program may be running than the check- summed one or because a verification tool may be corrupt. Scanning of the system may not identify such falsified code – it is very difficult to send something suspicious in a vast amount of code unless looking for a specific code or type of attack. Verification tests cannot send hidden code because they can only test for known problems and cannot predetermine all potential vectors of attack.
For example, in the insider fraud case mentioned earlier, a developer of the RNG system (Eddie Tipton) embedded a fraudulent software allowing him to manipulate draw outcomes. Tipton later became the Information Security Director for the Multi-State Lottery Association and his fraudulent software was only detected after many years. The fraudulent RNG was used for draws in at least 6 games played across 5 states. Tipton was caught due to the suspicious way in which he claimed a high prize and only during later investigations was the fraudulent software discovered when the type of attack was largely characterized (Clayworth, 2017; Khan, 2017). Tipton’s attack was not very sophisticated; however, it was very effective against a traditional RNG system whose protections are preventive in nature. In an RNG system with conclusive integrity problems’ detection, the fraud would have never succeeded, let alone continued for many years. RNG systems providing nonrepudiation of the draw numbers and verification of proof of integrity will ensure transparency for all parts of the draw: these systems will not allow attackers to implant or hide their fraudulent software.

Hardware deterioration: RNG Hardware may deteriorate over time, causing the RNG to malfunction and potentially lose its randomness property. Faulty hardware may still generate numbers without providing an external indication of hardware deterioration. Such a malfunction can also be fraudulently instigated by an attacker who substitutes RNG hardware to obtain predictable winning outcomes.
This type of problem is avoided by RNG systems that verify the integrity of the RNG seed during the draw. The Szrek system verifies hardware before proceeding with a draw. Should the verification fail due to a faulty HSM, the TD360 system automatically switches to use another Hardware Security Module (HSM). If both fail, the machine will not generate draw results and the Lottery is alerted to use a different draw machine or to correct the problem. Please note that signature verification is not a hardware status check but a hardware functionality verification.
Hardware substitution: RNG hardware can be substituted with a fraudulent hardware to obtain predictable winning outcomes for a specific draw. Unless there is a way to identify which hardware was used, the substitution of hardware can go unnoticed. This is a very similar case to 2, except that in this case hardware is substituted by an attacker.This type of problem is detected by RNG systems that use background cycling, that verify the integrity of the RNG seed during the draw, or that provide nonrepudiation and proof of integrity.
Substitution of numbers drawn: numbers may be simply replaced with other numbers if the RNG system does not provide verification methods. Herb Delehanty, consultant, refers to this as the “Low tech paper shuffle” where the draw results are on a sheet of paper that is simply replaced. Another example would be printing of the wrong data, possibly intentionally via a wifi connected printer. Delehanty (2017) argues that this is the easiest scam ever to implement and he suggests video and audio monitoring to help avoid this. A solution that detects what happens inside the system – one that provides proof of integrity – is the gold standard.

Draw time substitution: In an offline or isolated system, the system time cannot be continuously verified. This means that the time of a draw could be altered after the draw results are known by an insider. To detect time related fraud, draw nonrepudiation must include proof of the draw time. Verification of draw integrity will then confirm the actual draw time. Manipulation of draw time is protected by the HSM’s Real Time Clock. The Szrek RNG includes draw time in the Draw Signature which ensures detection of time related errors or attacks.
 Phishing: A traditional RNG, and in particular an offline system, may allow for multiple generations of draw results. This would allow an insider to continue phishing or searching for combinations until a desired draw result is found. This desired draw result could then be published as the proper draw outcome. Draw nonrepudiation must account for every random number generated. When draw integrity is independently verified, non-verified draws are detected providing proof of phishing.
Phishing: A traditional RNG, and in particular an offline system, may allow for multiple generations of draw results. This would allow an insider to continue phishing or searching for combinations until a desired draw result is found. This desired draw result could then be published as the proper draw outcome. Draw nonrepudiation must account for every random number generated. When draw integrity is independently verified, non-verified draws are detected providing proof of phishing.
![]()
Inadequate RNG design and implementation: There are multiple design and implementation issues that can make a RNG vulnerable including:
(i) the RNG algorithm may not be cryptographically strong – RNG certification by an independent party should include algorithm analysis and verification. There are many examples in which casinos have fallen victim to cheaters who have figured out how to beat the odds.
(ii) draw system software may not have built-in checks for hardware deterioration or malfunctions. Ideally,
 (iii) software errors or “bugs” may be present and configuration errors may exist. When draw systems are tested in a mode similar to live systems this may help identify problems. Certification should also be adequate and repeated when RNG software is altered. Systems should perform hardware checks before every draw. When hardware malfunctions occur the device may lose its randomness property as described above (point 2).
(iii) software errors or “bugs” may be present and configuration errors may exist. When draw systems are tested in a mode similar to live systems this may help identify problems. Certification should also be adequate and repeated when RNG software is altered. Systems should perform hardware checks before every draw. When hardware malfunctions occur the device may lose its randomness property as described above (point 2).