Deconstructing the RNG Black Box
This appeared first in the NASPL Insights Magazine.
Deconstucting the RNG
BLACK BOX
Security in the lottery industry is essential and a priority for all stakeholders. Players must trust that lotteries provide secure games and solutions, trusting RNGs and all other aspects of the lottery process. Some players may distrust RNGs because they perceive them as a ‘black box’, lacking transparency into the draw process. Actually, many currently existing draw solutions can be considered ‘gray boxes’, in that they provide security measures and procedures allowing some visibility into the draw process. However, the ‘gray box’ is not 100% safe, it may not protect against hardware problems or deterioration of hardware, and most likely will not protect against fraud by an insider attack. Past incidents, including repeated draw numbers and insider fraud have underscored the need for a ‘white box’ RNG, a solution that provides draw transparency and ensures that any draw problem will be detected by an independent audit.
Wikipedia definition: Black Box:
In science, computing, and engineering, a black box is a system which can be viewed in terms of its inputs and outputs, without any knowledge of its internal workings. Its implementation is “opaque” (black). To analyze an open system with a typical “black box approach”, only the behavior of the stimulus/response will be accounted for, to infer the (unknown) box.
The opposite of a black box is a system where the inner components or logic are available for inspection, which is most commonly referred to as a white box.
Preventive security measures and procedures used for draws typically protect only against known or foreseen types of problems. Some currently used preventive measures are sometimes referred to as a “security theater”, as they may seem good but do not add security value. For example, one of the lotteries that was using our systems in a secure enclosure installed alarms that would notify an external security company when the enclosure door was opened. In reality, if there were an attack, it would most likely come from a trusted insider who would know how to manipulate the system, and not from someone illegally trying to break through the secured cabinet to access the computer. After using our Trusted Audit system, which validates the integrity of the draw results, the lottery decided that the verification service was offering them more security than the alarm and stopped using the alarm service.
The lottery industry has experienced various incidents that reflect a need to move beyond traditional preventive security measures. MUSL drawing machines were operated in several states for several years, and none of their protections helped against insider fraud. Security measures were in place, the computer was in a locked glass-walled room accessible only by two people at a time and then only on camera, and it wasn’t connected to the Internet or any other networks. And yet, without complete transparency, the RNG was unable to detect that it had been compromised. In another situation, when lotteries experienced repeating random numbers over subsequent draws, was due to failed RNG hardware. In yet another example, raffle draws were held from incomplete ranges. All the preventive measures and procedures used did not detect these problems, hence our analogy of the ‘grey box’ – a system that lacks complete transparency and is unable to detect all problems.
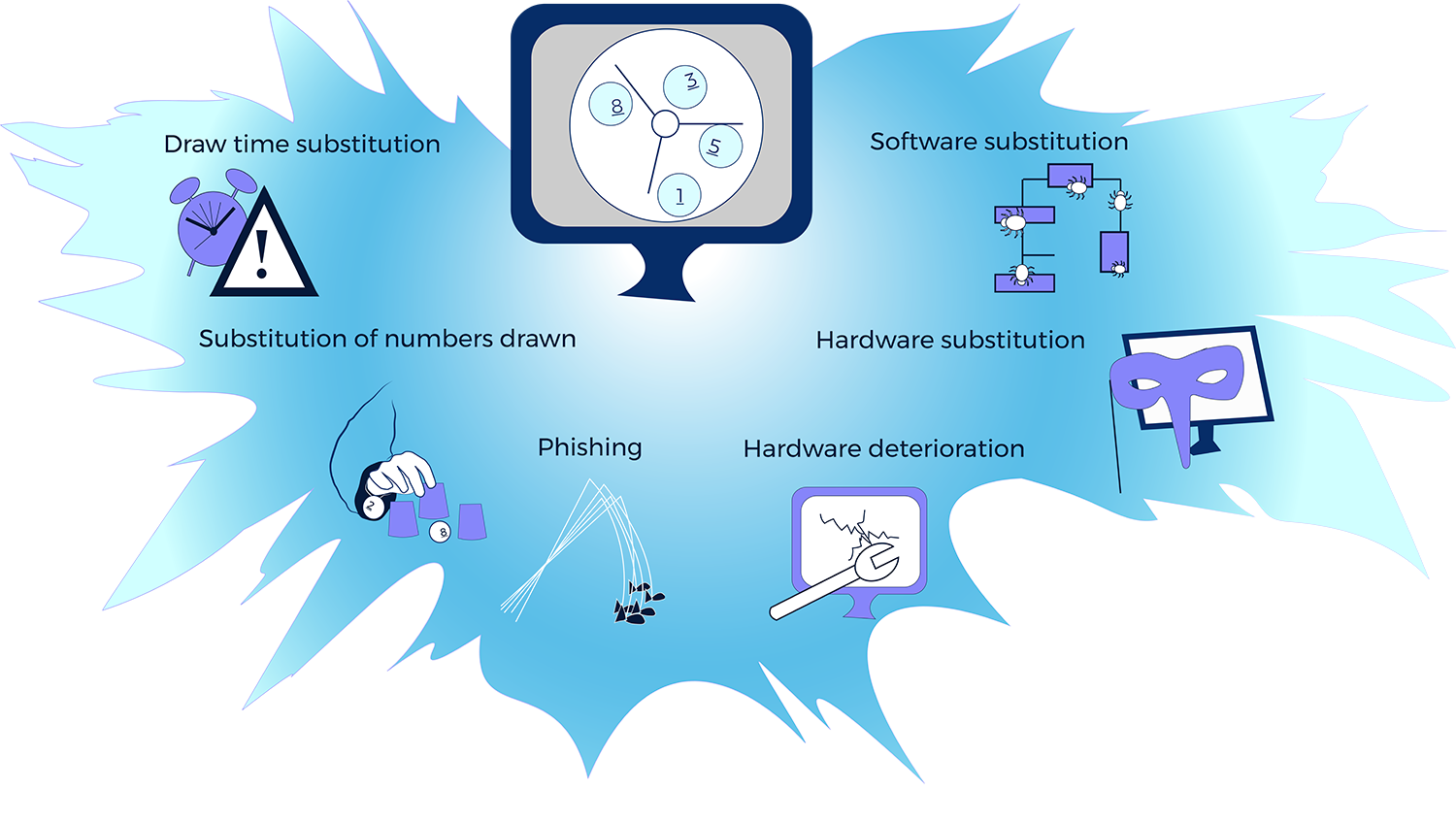
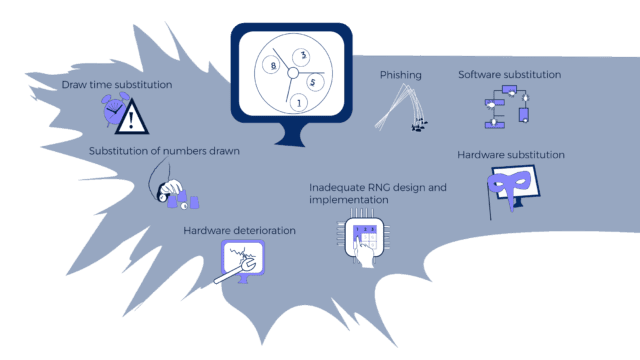
The vectors of attack see more here
Let’s illustrate the problem, using an analogy from banking:
Imagine someone deposited counterfeit money and the bank was unable to identify that the bills were forged. After the money is accepted by the cashier, it begins circulating in the bank’s system- it joins an existing electronic trail and works without further problems. The money could be transferred, it will accrue interest, and can be withdrawn. No audit would show any problems. In this way, when the fake money was accepted into the system, the security of the banking system failed. The same problem exists with random numbers. If the source of randomness is bad, due to RNG hardware failure or deterioration, or if there is draw manipulation that is not recognized, the random outcomes will be affected and corrupted.
In the case of a lottery draw, a ‘white box’ RNG would be able to detect any hardware or software failures, insider fraud, or changes made at any time to the draw results, and any other problem that could occur. In addition, a ‘white box’ solution can prove the validity of draw numbers. When unusual draw numbers, like numbers in sequence, are selected as winning numbers, as seen in December 2020 in South Africa’s draw of 5, 6, 7, 8, 9, 10, a ‘white box’ RNG is able to validate the random numbers as being true and correct.
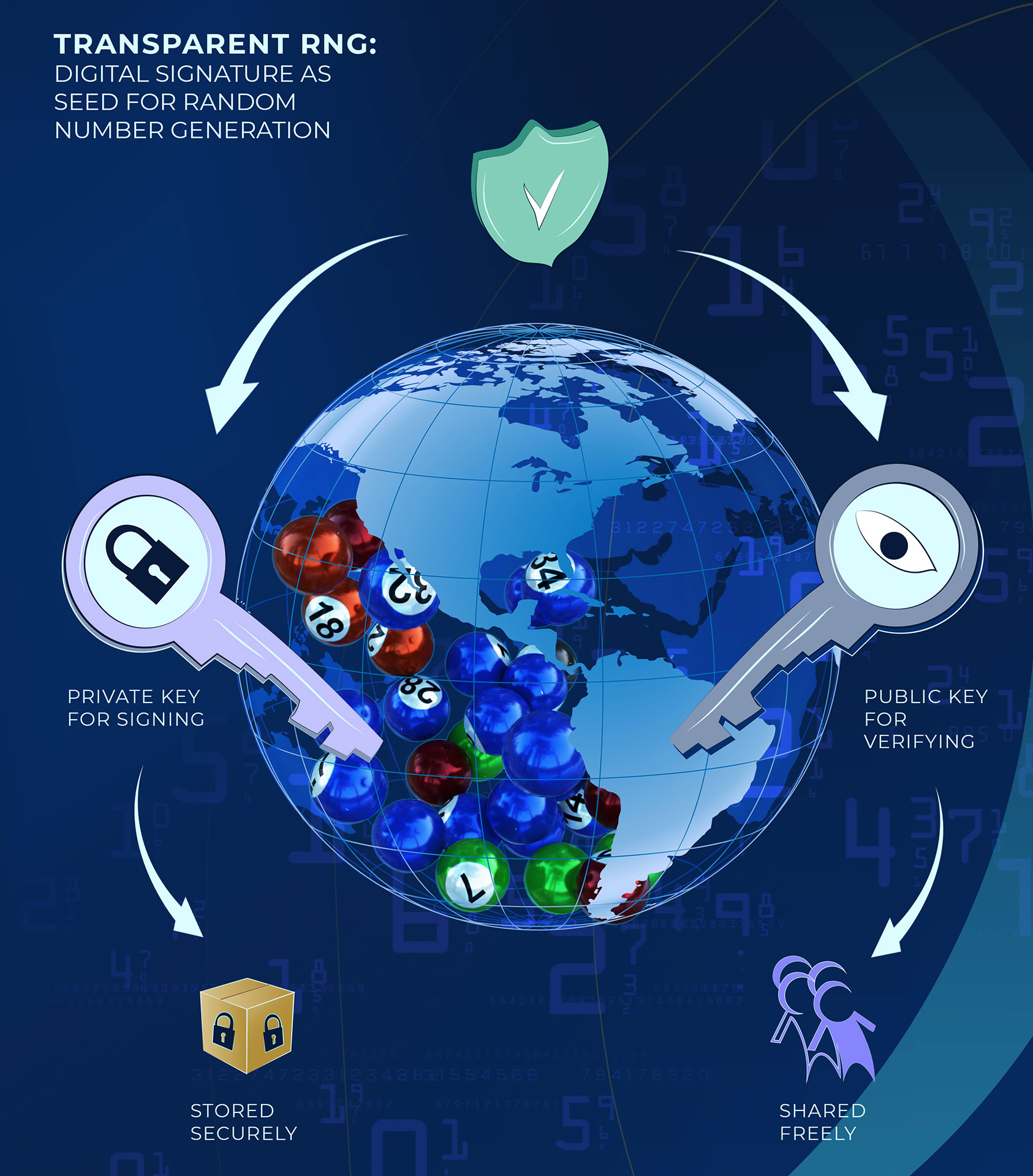
The existing ‘white box’ RNG solution is connected to the revolution in computing and cryptographic technology – brought by PKI (Public Key Infrastructure). The PKI technology enables secure communication over the Internet, Block Chains, Bit Coins and enables transparency in Random Numbers Generation.
PKI enables verification of data without knowing how it was created. If the RNG seed is created using PKI, e.g. using digital signatures as RNG seeds, we can verify that the seed is correct without knowing all information needed to generate it! To make the RNG system transparent, it is enough to generate the RNG seed with PKI technology and to transfer it to an independent verification system. Now, one can verify the correctness of the RNG seed and using the same RNG algorithm (PRNG), recreate the random numbers.
The main elements in the process are the algorithm and the RNG seed.
- The Algorithm: the PRNG algorithm transforms the seed data to the actual random numbers. It always generates the same set of numbers from the same input (seed). The PRNG algorithm needs to be cryptographically strong.
- RNG Seed: the seed provides the actual randomness and is unknown and unpredictable. The same seed will always create the same string of random numbers.
There are several benefits to using PKI technology for RNGs.
* Hardware faults are detected and ensure that hardware is not deteriorated during number generation.
* Some hardware devices keep independent verifiable time and a generation counter that allows to account for each random number generated and verify the time the draw took place.
* The verification process enables proving the integrity of the random results and the information of associated data such as the game matrix.
* If we provide the hash of bets participating in the draw, we also have proof of the content of the bets before the draw.
* If we provide player information for an instant win transaction, we can prove the outcome (win or loss) belongs to the specific player.
* In a connected environment, the verification system can be integrated with ICS.
-
-
- The verification process can be automated, with draw numbers automatically verified by ICS in real time.
- When the gaming system includes the hash of all bets with the draw request, the RNG system digitally signs the hash as a part of the RNG seed. The digitally signed hash of the bets can be verified by ICS in real time.
- Verification can be done for 5-minute Keno and other frequent draws.
- The hash of the file with 2nd chance draw data can be verified by ICS
-
As we conclude, we highlight the importance of RNG transparency. While errors, hardware or software malfunctions, human mistakes, and cases of fraud are bound to happen, problems persist because the random number generation process has not been transparent. Problems are hidden inside the ‘black box’ or not fully visible in a ‘grey box’, and because they are not evident externally, they can exist without being detected. The cost of a single problem is very high and hurts the whole industry. The lack of transparency in any part of the draw opens the industry to vulnerabilities that could be avoided by using the ‘white box’ solution.